I am hitting this with the following combination: 1) Browser incognito mode (Chrome) 2) Application is behind Azure application gateway (no repro if it isnt). Cookie based affinity is turned OFF (default); if turned ON, seems to make repro happen more often.
Code is rather plain vanilla OIDC authN + cookies.
services.AddAuthentication(options =>
{
options.DefaultScheme = CookieAuthenticationDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme;
})
.AddAzureAd(options => {
Configuration.Bind("AzureAd", options);
})
.AddCookie(p => p.SlidingExpiration = true);
I am forwarding the X-Forwarded-Proto header to the auth middleware as recommended so the redirect_uri uses the correct protocol scheme.
HANDLING IN CODE
I tried to handle the OnRemoteFailure() event, and redirect to "/Home/AuthRedirect" which is an anon page that waits for 20 secs, and then redirects to the "/" (home page). It seems to work sometimes, but not always. I am out of ideas.
WORKAROUND
1) Users can go to the homepage again and hit F5 until this works. It seems that each F5 gets them moving a step ahead and once the OpenID cookies are populated, everything else (I have more auth after openid finishes, via adal.js for AJAX use). 2) Bypass the application gateway and use the direct service fabric cluster DNS name (not acceptable as it is http).
DETAILS
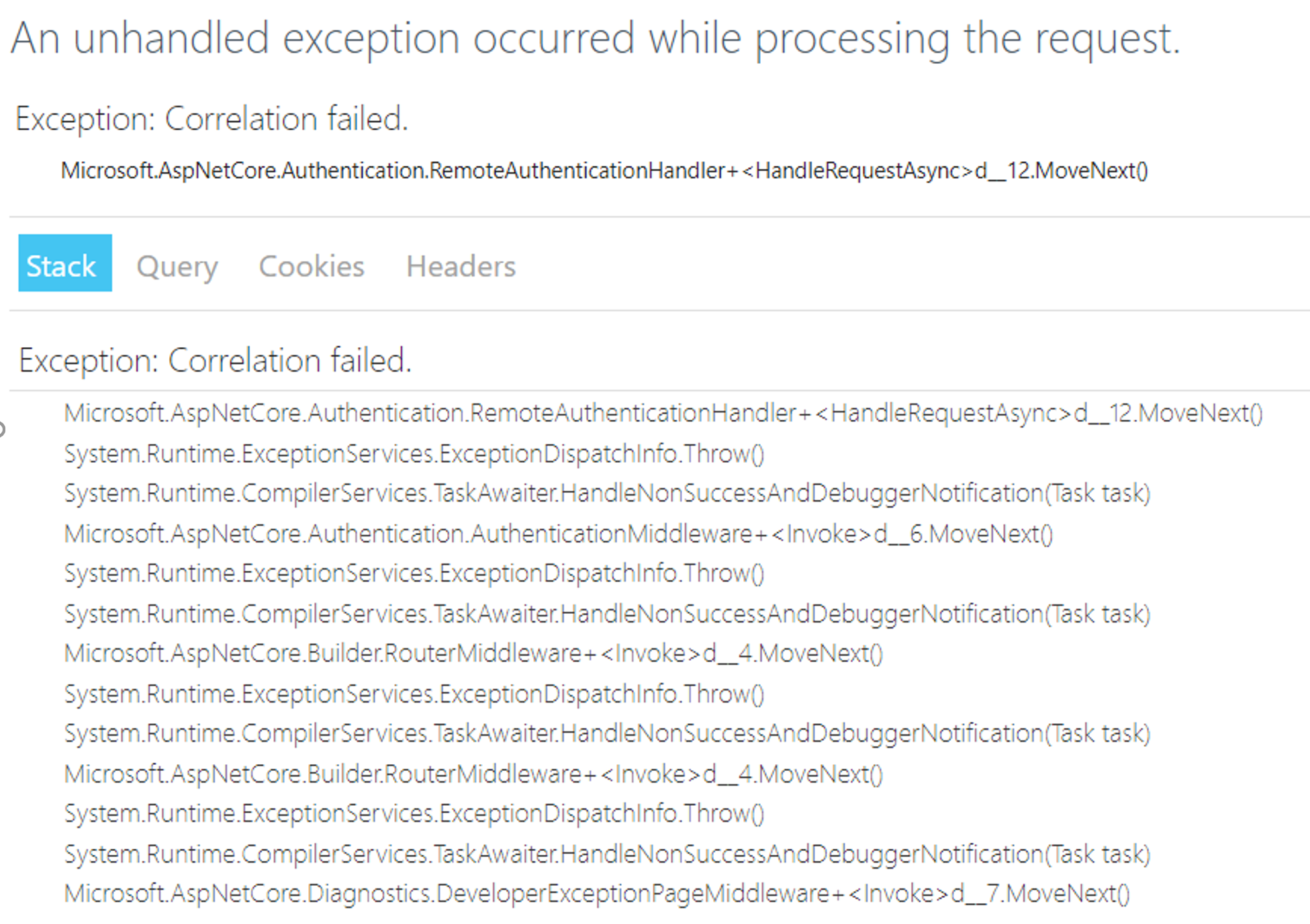
System.Exception: Correlation failed. at Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler`1.d__12.MoveNext() --- End of stack trace from previous location where exception was thrown --- at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task) at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.d__6.MoveNext() --- End of stack trace from previous location where exception was thrown --- at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task) at Microsoft.AspNetCore.Builder.RouterMiddleware.d__4.MoveNext() --- End of stack trace from previous location where exception was thrown --- at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task) at Microsoft.AspNetCore.Builder.RouterMiddleware.d__4.MoveNext() --- End of stack trace from previous location where exception was thrown --- at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task) at Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddleware.d__7.MoveNext()
I had the same problem, but my issue was due to my understanding of auth workflow, which was wrong. There are two callback URLs that are important, and I thought they serve the same purpose. I was so wrong.
This is defined in Startup.cs
It tells the authorisation middleware in your app, on which URL it should listen, once auth provider gets back after successful authentication. Then the middleware itself will redirect the application to the callback URL defined in your Login action (sample code is below).
After that (two days of struggle), everything started working.
I have same problem, if your environment is web farm, you should use DataProtection to share key.
I had the same issue. I was defining multiple external endpoints for Authorization. In my case I had defined Callback Paths that were being used by multiple clients. Once I defined unique Callback Paths the problem was solved: example:
Similarly, make sure the
SignedOutCallbackPathsare unique. Hope it works for you.